穷追非明码算法的注册码+算法注册机|一蓑烟雨论坛|UpkSafe|Upk安 算法注册机
【文章作者】: BeyondMe
【作者邮箱】: futuring@126.com
【作者主页】: http://hi.baidu.com/beyond0769
【软件名称】: Flash Screensaver Maker Simple Version V3.7
【下载地址】: http://www.softboy.net/flash2scr/
【软件介绍】: 可以将Flash文件轻松转换成scr屏保。
【作者声明】: 只是感兴趣,没有其他目的。失误之处敬请诸位大侠赐教!
--------------------------------------------------------------------------------
【详细过程】
这是一个典型的非明码比较,设置多重验证的算法过程,分析起来非常有意思。适合有耐心的破友 ^_^
无技术含量,大鸟飞过~~~~
第一关:下断的问题。
OD载入运行马上弹出注册对话框,输入假码:12345678909876543210ABCD (共24位)
至于为什么要24位,后面分析。
出现错误提示:sorry, registration code is not right, Try again 字样。
查超级字符串,一无所获,郁闷 ~~~ ,bp MessageBoxA 无法断下,郁闷 ~~~
再试 bp MessageBoxExA ,失败,最后试 bp MessageBoxExW,还是不行,看来试图在消息框下断的希望没了。
然后在提示注册失败后,程序会打开它的主页,这一动作给你提示什么,程序估计调用API函数ShellExecuteExA,
于是下断 bp ShellExecuteExA,成功断下,返回到主算法过程:
0040B734 /. 55 PUSH EBP ; 主算法过程
0040B735 |. 8BEC MOV EBP,ESP
0040B737 |. 83C4 9C ADD ESP,-64
0040B73A |. 8955 A0 MOV DWORD PTR SS:[EBP-60],EDX
0040B73D |. 8945 A4 MOV DWORD PTR SS:[EBP-5C],EAX
0040B740 |. B8 E07F4C00 MOV EAX,Flash2SC.004C7FE0
0040B745 |. E8 DACE0A00 CALL Flash2SC.004B8624
0040B74A |. 8B15 14134D00 MOV EDX,DWORD PTR DS:[4D1314] ; Flash2SC._Form1
0040B750 |. 8B0A MOV ECX,DWORD PTR DS:[EDX]
0040B752 |. 80B9 DC050000>CMP BYTE PTR DS:[ECX+5DC],0 ; 是否已经注册?(=0未注册,不等于0已经注册)
0040B759 |. 0F85 49030000 JNZ Flash2SC.0040BAA8
0040B75F |. 8B45 A4 MOV EAX,DWORD PTR SS:[EBP-5C]
0040B762 |. 8B90 3C030000 MOV EDX,DWORD PTR DS:[EAX+33C]
0040B768 |. 807A 57 00 CMP BYTE PTR DS:[EDX+57],0
0040B76C 0F84 8E000000 JE Flash2SC.0040B800 ; 注册码输入了吗?
0040B772 |. 66:C745 B8 08>MOV WORD PTR SS:[EBP-48],8
0040B778 |. 8D45 FC LEA EAX,DWORD PTR SS:[EBP-4]
0040B77B |. E8 5464FFFF CALL Flash2SC.00401BD4
0040B780 |. 8BD0 MOV EDX,EAX
0040B782 |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B785 |. 8B4D A4 MOV ECX,DWORD PTR SS:[EBP-5C]
0040B788 |. 8B81 3C030000 MOV EAX,DWORD PTR DS:[ECX+33C]
0040B78E |. E8 19DA0500 CALL Flash2SC.004691AC
0040B793 |. 8D45 FC LEA EAX,DWORD PTR SS:[EBP-4]
0040B796 |. E8 E9A9FFFF CALL Flash2SC.00406184
0040B79B |. 83F8 03 CMP EAX,3
0040B79E |. 0F9CC2 SETL DL
0040B7A1 |. 83E2 01 AND EDX,1
0040B7A4 |. 52 PUSH EDX ; /Arg1
0040B7A5 |. FF4D C4 DEC DWORD PTR SS:[EBP-3C] ; |
0040B7A8 |. 8D45 FC LEA EAX,DWORD PTR SS:[EBP-4] ; |
0040B7AB |. BA 02000000 MOV EDX,2 ; |
0040B7B0 |. E8 EB6F0B00 CALL Flash2SC.004C27A0 ; Flash2SC.004C27A0
0040B7B5 |. 59 POP ECX
0040B7B6 |. 84C9 TEST CL,CL
0040B7B8 |. 74 3C JE SHORT Flash2SC.0040B7F6
0040B7BA |. 66:C745 B8 14>MOV WORD PTR SS:[EBP-48],14
0040B7C0 |. BA 647A4C00 MOV EDX,Flash2SC.004C7A64 ; ASCII "Please input your Full Name!"
0040B7C5 |. 8D45 F8 LEA EAX,DWORD PTR SS:[EBP-8]
0040B7C8 |. E8 376E0B00 CALL Flash2SC.004C2604
0040B7CD |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B7D0 |. 8B00 MOV EAX,DWORD PTR DS:[EAX]
0040B7D2 |. E8 417D0500 CALL Flash2SC.00463518
0040B7D7 |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040B7DA |. 8D45 F8 LEA EAX,DWORD PTR SS:[EBP-8]
0040B7DD |. BA 02000000 MOV EDX,2
0040B7E2 |. E8 B96F0B00 CALL Flash2SC.004C27A0
0040B7E7 |. 8B4D A8 MOV ECX,DWORD PTR SS:[EBP-58]
0040B7EA |. 64:890D 00000>MOV DWORD PTR FS:[0],ECX
0040B7F1 |. E9 C4020000 JMP Flash2SC.0040BABA
0040B7F6 |> 68 F4010000 PUSH 1F4 ; /Timeout = 500. ms
0040B7FB |. E8 F8790B00 CALL <JMP.&kernel32.Sleep> ; 先睡上一觉 Sleep(500)
0040B800 |. 66:C745 B8 20>MOV WORD PTR SS:[EBP-48],20 ; 不知为什么,老外就喜欢睡觉。
0040B806 |. 8D45 F4 LEA EAX,DWORD PTR SS:[EBP-C]
0040B809 |. E8 C663FFFF CALL Flash2SC.00401BD4
0040B80E |. 8BD0 MOV EDX,EAX
0040B810 |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B813 |. 8B4D A4 MOV ECX,DWORD PTR SS:[EBP-5C]
0040B816 |. 8B81 FC020000 MOV EAX,DWORD PTR DS:[ECX+2FC]
0040B81C |. E8 8BD90500 CALL Flash2SC.004691AC
0040B821 |. 8D55 F4 LEA EDX,DWORD PTR SS:[EBP-C]
0040B824 |. FF32 PUSH DWORD PTR DS:[EDX] ; /Arg2
0040B826 |. 68 507D4D00 PUSH Flash2SC.004D7D50 ; |Arg1 = 004D7D50
0040B82B |. E8 7CFBFFFF CALL Flash2SC.0040B3AC ; 关键算法,F7进入
0040B830 |. 83C4 08 ADD ESP,8
0040B833 |. 8B0D 14134D00 MOV ECX,DWORD PTR DS:[4D1314] ; Flash2SC._Form1
0040B839 |. 8B11 MOV EDX,DWORD PTR DS:[ECX]
0040B83B |. 8882 DC050000 MOV BYTE PTR DS:[EDX+5DC],AL
0040B841 |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040B844 |. 8D45 F4 LEA EAX,DWORD PTR SS:[EBP-C]
0040B847 |. BA 02000000 MOV EDX,2
0040B84C |. E8 4F6F0B00 CALL Flash2SC.004C27A0
0040B851 |. A1 14134D00 MOV EAX,DWORD PTR DS:[4D1314]
0040B856 |. 8B08 MOV ECX,DWORD PTR DS:[EAX]
0040B858 |. 80B9 DC050000>CMP BYTE PTR DS:[ECX+5DC],0 ; 是否已经注册了呢/
0040B85F |. 0F84 EF010000 JE Flash2SC.0040BA54 ; 注册成功不跳
0040B865 |. 66:C745 B8 2C>MOV WORD PTR SS:[EBP-48],2C ; 然后把注册信息保存在注册表里面
0040B86B |. 8D45 F0 LEA EAX,DWORD PTR SS:[EBP-10]
0040B86E |. E8 6163FFFF CALL Flash2SC.00401BD4
0040B873 |. 8BD0 MOV EDX,EAX
0040B875 |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B878 |. 8B4D A4 MOV ECX,DWORD PTR SS:[EBP-5C]
0040B87B |. 8B81 FC020000 MOV EAX,DWORD PTR DS:[ECX+2FC]
0040B881 |. E8 26D90500 CALL Flash2SC.004691AC
0040B886 |. 8D55 F0 LEA EDX,DWORD PTR SS:[EBP-10]
0040B889 |. 8B45 A4 MOV EAX,DWORD PTR SS:[EBP-5C]
0040B88C |. 05 40030000 ADD EAX,340
0040B891 |. E8 3A6F0B00 CALL Flash2SC.004C27D0
0040B896 |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040B899 |. 8D45 F0 LEA EAX,DWORD PTR SS:[EBP-10]
0040B89C |. BA 02000000 MOV EDX,2
0040B8A1 |. E8 FA6E0B00 CALL Flash2SC.004C27A0
0040B8A6 |. 8B55 A4 MOV EDX,DWORD PTR SS:[EBP-5C]
0040B8A9 |. 81C2 40030000 ADD EDX,340
0040B8AF |. A1 14134D00 MOV EAX,DWORD PTR DS:[4D1314]
0040B8B4 |. 8B00 MOV EAX,DWORD PTR DS:[EAX]
0040B8B6 |. 05 E0050000 ADD EAX,5E0
0040B8BB |. E8 106F0B00 CALL Flash2SC.004C27D0
0040B8C0 |. B2 01 MOV DL,1
0040B8C2 |. A1 DCDE4900 MOV EAX,DWORD PTR DS:[49DEDC]
0040B8C7 |. E8 10270900 CALL Flash2SC.0049DFDC
0040B8CC |. 8945 9C MOV DWORD PTR SS:[EBP-64],EAX
0040B8CF |. BA 01000080 MOV EDX,80000001
0040B8D4 |. 8B45 9C MOV EAX,DWORD PTR SS:[EBP-64]
0040B8D7 |. E8 946C0B00 CALL Flash2SC.004C2570
0040B8DC |. 66:C745 B8 38>MOV WORD PTR SS:[EBP-48],38
0040B8E2 |. BA 817A4C00 MOV EDX,Flash2SC.004C7A81 ; ASCII "SoftwareXTZYFlash2SCR"
0040B8E7 |. 8D45 EC LEA EAX,DWORD PTR SS:[EBP-14]
0040B8EA |. E8 156D0B00 CALL Flash2SC.004C2604
0040B8EF |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B8F2 |. 8B10 MOV EDX,DWORD PTR DS:[EAX]
0040B8F4 |. B1 01 MOV CL,1
0040B8F6 |. 8B45 9C MOV EAX,DWORD PTR SS:[EBP-64]
0040B8F9 |. E8 E6270900 CALL Flash2SC.0049E0E4
0040B8FE |. 50 PUSH EAX ; /Arg1
0040B8FF |. FF4D C4 DEC DWORD PTR SS:[EBP-3C] ; |
0040B902 |. 8D45 EC LEA EAX,DWORD PTR SS:[EBP-14] ; |
0040B905 |. BA 02000000 MOV EDX,2 ; |
0040B90A |. E8 916E0B00 CALL Flash2SC.004C27A0 ; Flash2SC.004C27A0
0040B90F |. 59 POP ECX
0040B910 |. 84C9 TEST CL,CL
0040B912 |. 0F84 C2000000 JE Flash2SC.0040B9DA
0040B918 |. 8D45 E4 LEA EAX,DWORD PTR SS:[EBP-1C]
0040B91B |. E8 B462FFFF CALL Flash2SC.00401BD4
0040B920 |. 8BD0 MOV EDX,EAX
0040B922 |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B925 |. 8B4D A4 MOV ECX,DWORD PTR SS:[EBP-5C]
0040B928 |. 8B81 FC020000 MOV EAX,DWORD PTR DS:[ECX+2FC]
0040B92E |. E8 79D80500 CALL Flash2SC.004691AC
0040B933 |. 8D55 E4 LEA EDX,DWORD PTR SS:[EBP-1C]
0040B936 |. FF32 PUSH DWORD PTR DS:[EDX]
0040B938 |. 66:C745 B8 44>MOV WORD PTR SS:[EBP-48],44
0040B93E |. BA 997A4C00 MOV EDX,Flash2SC.004C7A99 ; ASCII "NO"
0040B943 |. 8D45 E8 LEA EAX,DWORD PTR SS:[EBP-18]
0040B946 |. E8 B96C0B00 CALL Flash2SC.004C2604
0040B94B |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B94E |. 8B10 MOV EDX,DWORD PTR DS:[EAX]
0040B950 |. 8B45 9C MOV EAX,DWORD PTR SS:[EBP-64]
0040B953 |. 59 POP ECX
0040B954 |. E8 072B0900 CALL Flash2SC.0049E460
0040B959 |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040B95C |. 8D45 E4 LEA EAX,DWORD PTR SS:[EBP-1C]
0040B95F |. BA 02000000 MOV EDX,2
0040B964 |. E8 376E0B00 CALL Flash2SC.004C27A0
0040B969 |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040B96C |. 8D45 E8 LEA EAX,DWORD PTR SS:[EBP-18]
0040B96F |. BA 02000000 MOV EDX,2
0040B974 |. E8 276E0B00 CALL Flash2SC.004C27A0
0040B979 |. 8D45 DC LEA EAX,DWORD PTR SS:[EBP-24]
0040B97C |. E8 5362FFFF CALL Flash2SC.00401BD4
0040B981 |. 8BD0 MOV EDX,EAX
0040B983 |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B986 |. 8B4D A4 MOV ECX,DWORD PTR SS:[EBP-5C]
0040B989 |. 8B81 3C030000 MOV EAX,DWORD PTR DS:[ECX+33C]
0040B98F |. E8 18D80500 CALL Flash2SC.004691AC
0040B994 |. 8D55 DC LEA EDX,DWORD PTR SS:[EBP-24]
0040B997 |. FF32 PUSH DWORD PTR DS:[EDX]
0040B999 |. 66:C745 B8 50>MOV WORD PTR SS:[EBP-48],50
0040B99F |. BA 9C7A4C00 MOV EDX,Flash2SC.004C7A9C ; ASCII "Name"
0040B9A4 |. 8D45 E0 LEA EAX,DWORD PTR SS:[EBP-20]
0040B9A7 |. E8 586C0B00 CALL Flash2SC.004C2604
0040B9AC |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040B9AF |. 8B10 MOV EDX,DWORD PTR DS:[EAX]
0040B9B1 |. 8B45 9C MOV EAX,DWORD PTR SS:[EBP-64]
0040B9B4 |. 59 POP ECX
0040B9B5 |. E8 A62A0900 CALL Flash2SC.0049E460
0040B9BA |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040B9BD |. 8D45 DC LEA EAX,DWORD PTR SS:[EBP-24]
0040B9C0 |. BA 02000000 MOV EDX,2
0040B9C5 |. E8 D66D0B00 CALL Flash2SC.004C27A0
0040B9CA |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040B9CD |. 8D45 E0 LEA EAX,DWORD PTR SS:[EBP-20]
0040B9D0 |. BA 02000000 MOV EDX,2
0040B9D5 |. E8 C66D0B00 CALL Flash2SC.004C27A0
0040B9DA |> 8B45 9C MOV EAX,DWORD PTR SS:[EBP-64]
0040B9DD |. E8 6A260900 CALL Flash2SC.0049E04C
0040B9E2 |. 8B55 9C MOV EDX,DWORD PTR SS:[EBP-64]
0040B9E5 |. 8955 D4 MOV DWORD PTR SS:[EBP-2C],EDX
0040B9E8 |. 837D D4 00 CMP DWORD PTR SS:[EBP-2C],0
0040B9EC |. 74 21 JE SHORT Flash2SC.0040BA0F
0040B9EE |. 8B4D D4 MOV ECX,DWORD PTR SS:[EBP-2C]
0040B9F1 |. 8B01 MOV EAX,DWORD PTR DS:[ECX]
0040B9F3 |. 8945 D8 MOV DWORD PTR SS:[EBP-28],EAX
0040B9F6 |. 66:C745 B8 68>MOV WORD PTR SS:[EBP-48],68
0040B9FC |. BA 03000000 MOV EDX,3
0040BA01 |. 8B45 D4 MOV EAX,DWORD PTR SS:[EBP-2C]
0040BA04 |. 8B08 MOV ECX,DWORD PTR DS:[EAX]
0040BA06 |. FF51 FC CALL DWORD PTR DS:[ECX-4]
0040BA09 |. 66:C745 B8 5C>MOV WORD PTR SS:[EBP-48],5C
0040BA0F |> 66:C745 B8 74>MOV WORD PTR SS:[EBP-48],74
0040BA15 |. 8D45 D0 LEA EAX,DWORD PTR SS:[EBP-30]
0040BA18 |. E8 B761FFFF CALL Flash2SC.00401BD4
0040BA1D |. 8BD0 MOV EDX,EAX
0040BA1F |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040BA22 |. 8B4D A4 MOV ECX,DWORD PTR SS:[EBP-5C]
0040BA25 |. 8B81 20030000 MOV EAX,DWORD PTR DS:[ECX+320]
0040BA2B |. E8 7CD70500 CALL Flash2SC.004691AC
0040BA30 |. 8D45 D0 LEA EAX,DWORD PTR SS:[EBP-30]
0040BA33 |. 8B00 MOV EAX,DWORD PTR DS:[EAX]
0040BA35 |. E8 DE7A0500 CALL Flash2SC.00463518
0040BA3A |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040BA3D |. 8D45 D0 LEA EAX,DWORD PTR SS:[EBP-30]
0040BA40 |. BA 02000000 MOV EDX,2
0040BA45 |. E8 566D0B00 CALL Flash2SC.004C27A0
0040BA4A |. 8B45 A4 MOV EAX,DWORD PTR SS:[EBP-5C]
0040BA4D |. E8 FAD00400 CALL Flash2SC.00458B4C
0040BA52 |. EB 5C JMP SHORT Flash2SC.0040BAB0
0040BA54 |> 66:C745 B8 80>MOV WORD PTR SS:[EBP-48],80
0040BA5A |. 8D45 CC LEA EAX,DWORD PTR SS:[EBP-34]
0040BA5D |. E8 7261FFFF CALL Flash2SC.00401BD4
0040BA62 |. 8BD0 MOV EDX,EAX
0040BA64 |. FF45 C4 INC DWORD PTR SS:[EBP-3C]
0040BA67 |. 8B4D A4 MOV ECX,DWORD PTR SS:[EBP-5C]
0040BA6A |. 8B81 1C030000 MOV EAX,DWORD PTR DS:[ECX+31C]
0040BA70 |. E8 37D70500 CALL Flash2SC.004691AC
0040BA75 |. 8D45 CC LEA EAX,DWORD PTR SS:[EBP-34]
0040BA78 |. 8B00 MOV EAX,DWORD PTR DS:[EAX]
0040BA7A |. E8 997A0500 CALL Flash2SC.00463518
0040BA7F |. FF4D C4 DEC DWORD PTR SS:[EBP-3C]
0040BA82 |. 8D45 CC LEA EAX,DWORD PTR SS:[EBP-34]
0040BA85 |. BA 02000000 MOV EDX,2
0040BA8A |. E8 116D0B00 CALL Flash2SC.004C27A0
0040BA8F EB 1F JMP SHORT Flash2SC.0040BAB0 ; 修改一下,免得每次注册失败都弹出这个讨厌的主页
0040BA91 |. 6A 00 PUSH 0 ; |DefDir = NULL
0040BA93 |. 6A 00 PUSH 0 ; |Parameters = NULL
0040BA95 |. 68 A67A4C00 PUSH Flash2SC.004C7AA6 ; |FileName = "http://www.softboy.net/flash2scr"
0040BA9A |. 68 A17A4C00 PUSH Flash2SC.004C7AA1 ; |Operation = "open"
0040BA9F |. 6A 00 PUSH 0 ; |hWnd = NULL
0040BAA1 |. E8 747A0B00 CALL <JMP.&SHELL32.ShellExecuteA> ; ShellExecuteA
0040BAA6 |. EB 08 JMP SHORT Flash2SC.0040BAB0
0040BAA8 |> 8B45 A4 MOV EAX,DWORD PTR SS:[EBP-5C]
0040BAAB |. E8 9CD00400 CALL Flash2SC.00458B4C
0040BAB0 |> 8B55 A8 MOV EDX,DWORD PTR SS:[EBP-58]
0040BAB3 |. 64:8915 00000>MOV DWORD PTR FS:[0],EDX
0040BABA |> 8BE5 MOV ESP,EBP
0040BABC |. 5D POP EBP
0040BABD . C3 RETN
其实还有可以通过 bpx Sleep 来下断,老外就喜欢睡觉,没办法。-_-!!
主程序没有什么好说的,进入其关键算法过程
0040B82B |. E8 7CFBFFFF CALL Flash2SC.0040B3AC ; 关键算法,F7进入
0040B3AC /$ 55 PUSH EBP ; 关键算法
0040B3AD |. 8BEC MOV EBP,ESP
0040B3AF |. 81C4 3CFFFFFF ADD ESP,-0C4
0040B3B5 |. 56 PUSH ESI
0040B3B6 |. 57 PUSH EDI
0040B3B7 |. B8 F07E4C00 MOV EAX,Flash2SC.004C7EF0
0040B3BC |. E8 63D20A00 CALL Flash2SC.004B8624
0040B3C1 |. C745 F8 01000>MOV DWORD PTR SS:[EBP-8],1
0040B3C8 |. 8D55 0C LEA EDX,DWORD PTR SS:[EBP+C]
0040B3CB |. 8D45 0C LEA EAX,DWORD PTR SS:[EBP+C]
0040B3CE |. E8 69720B00 CALL Flash2SC.004C263C
0040B3D3 |. FF45 F8 INC DWORD PTR SS:[EBP-8]
0040B3D6 |. 66:C745 EC 08>MOV WORD PTR SS:[EBP-14],8
0040B3DC |. C645 DB 00 MOV BYTE PTR SS:[EBP-25],0 ; 标志位赋值=0(注册失败)
0040B3E0 |. 8D45 0C LEA EAX,DWORD PTR SS:[EBP+C]
0040B3E3 |. E8 9CADFFFF CALL Flash2SC.00406184
0040B3E8 |. 83F8 18 CMP EAX,18 ; 如果注册码长度为和24比较
0040B3EB |. 0F85 88000000 JNZ Flash2SC.0040B479 ; 不相等则跳
0040B3F1 |. BE 307A4C00 MOV ESI,Flash2SC.004C7A30 ; ASCII "1y1h+2a0n-0g8z*9a1n|"
0040B3F6 |. 8D7D 94 LEA EDI,DWORD PTR SS:[EBP-6C]
0040B3F9 |. B9 05000000 MOV ECX,5
0040B3FE |. F3:A5 REP MOVS DWORD PTR ES:[EDI],DWORD PTR DS>
0040B400 |. A4 MOVS BYTE PTR ES:[EDI],BYTE PTR DS:[ESI]
0040B401 |. 8D45 0C LEA EAX,DWORD PTR SS:[EBP+C]
0040B404 |. E8 0B78FFFF CALL Flash2SC.00402C14 ; 假码。记为Sn
0040B409 |. 50 PUSH EAX ; /Arg2
0040B40A |. 8D55 AC LEA EDX,DWORD PTR SS:[EBP-54] ; |
0040B40D |. 52 PUSH EDX ; |Arg1
0040B40E |. E8 99CF0A00 CALL Flash2SC.004B83AC ; Flash2SC.004B83AC
0040B413 |. 83C4 08 ADD ESP,8
0040B416 |. C645 DB 01 MOV BYTE PTR SS:[EBP-25],1 ; 标志位赋值=1(注册成功)
0040B41A |. 33C9 XOR ECX,ECX
0040B41C |. 894D D4 MOV DWORD PTR SS:[EBP-2C],ECX
0040B41F |> 8B45 D4 /MOV EAX,DWORD PTR SS:[EBP-2C]
0040B422 |. 40 |INC EAX
0040B423 |. B9 05000000 |MOV ECX,5
0040B428 |. 99 |CDQ
0040B429 |. F7F9 |IDIV ECX
0040B42B |. 85D2 |TEST EDX,EDX
0040B42D |. 74 3D |JE SHORT Flash2SC.0040B46C ; if n mod 5 = 0 then Continue (继续取下一位)
0040B42F |. 8B45 08 |MOV EAX,DWORD PTR SS:[EBP+8]
0040B432 |. 8B55 D4 |MOV EDX,DWORD PTR SS:[EBP-2C]
0040B435 |. 8A0C10 |MOV CL,BYTE PTR DS:[EAX+EDX]
0040B438 |. 8B45 D4 |MOV EAX,DWORD PTR SS:[EBP-2C]
0040B43B |. 324C05 94 |XOR CL,BYTE PTR SS:[EBP+EAX-6C]
0040B43F |. 0FBED1 |MOVSX EDX,CL
0040B442 |. 52 |PUSH EDX ; /Arg1
0040B443 |. E8 28020000 |CALL Flash2SC.0040B670 ; Flash2SC.0040B670
0040B448 |. 59 |POP ECX
0040B449 |. 69C0 3D220000 |IMUL EAX,EAX,223D
0040B44F |. B9 1A000000 |MOV ECX,1A
0040B454 |. 99 |CDQ
0040B455 |. F7F9 |IDIV ECX
0040B457 |. 83C2 41 |ADD EDX,41
0040B45A |. 8B45 D4 |MOV EAX,DWORD PTR SS:[EBP-2C]
0040B45D |. 0FBE4C05 AC |MOVSX ECX,BYTE PTR SS:[EBP+EAX-54]
0040B462 |. 3BD1 |CMP EDX,ECX
0040B464 |. 74 06 |JE SHORT Flash2SC.0040B46C ; 如果算法结果不相等,失败
0040B466 |. C645 DB 00 |MOV BYTE PTR SS:[EBP-25],0 ; 标志位赋值=0(注册失败)
0040B46A |. EB 09 |JMP SHORT Flash2SC.0040B475
0040B46C |> FF45 D4 |INC DWORD PTR SS:[EBP-2C]
0040B46F |. 837D D4 14 |CMP DWORD PTR SS:[EBP-2C],14 ; 循环范围是20次
0040B473 |.^7C AA JL SHORT Flash2SC.0040B41F ; 循环结束后下一句就是
0040B475 |> C645 DB 00 MOV BYTE PTR SS:[EBP-25],0 ; 标志位赋值=0(注册失败)
0040B479 |> 8D45 0C LEA EAX,DWORD PTR SS:[EBP+C] ; 以上循环不管怎么算,都是注册失败
0040B47C |. E8 03ADFFFF CALL Flash2SC.00406184 ; 假码长度
0040B481 |. 83F8 2A CMP EAX,2A ; 和42比较,
0040B484 |. 0F85 BE010000 JNZ Flash2SC.0040B648 ; 如果不相等,注册失败
……以下暂时省略……
进入关键算法过程后,程序获得假码的长度,和24比较,如果相等则进行上述循环中计算。
我们不急着看循环详细步骤,且看前后的意义
在进入循环前,程序就将标志位赋值为1,表注册通过,
0040B416 |. C645 DB 01 MOV BYTE PTR SS:[EBP-25],1 ; 标志位赋值=1(注册成功)
然而,通过其下面一个循环,无论计算比较结果是否相等,都把注册标志赋值为0,失败
再次引用上述循环的尾部看看:
0040B45D |. 0FBE4C05 AC |MOVSX ECX,BYTE PTR SS:[EBP+EAX-54]
0040B462 |. 3BD1 |CMP EDX,ECX
0040B464 |. 74 06 |JE SHORT Flash2SC.0040B46C ; 如果算法结果不相等,失败
0040B466 |. C645 DB 00 |MOV BYTE PTR SS:[EBP-25],0 ; 标志位赋值=0(注册失败)
0040B46A |. EB 09 |JMP SHORT Flash2SC.0040B475
0040B46C |> FF45 D4 |INC DWORD PTR SS:[EBP-2C]
0040B46F |. 837D D4 14 |CMP DWORD PTR SS:[EBP-2C],14 ; 循环范围是20次
0040B473 |.^ 7C AA JL SHORT Flash2SC.0040B41F ; 循环结束后下一句就是
0040B475 |> C645 DB 00 MOV BYTE PTR SS:[EBP-25],0 ; 标志位赋值=0(注册失败)
0040B479 |> 8D45 0C LEA EAX,DWORD PTR SS:[EBP+C] ; 以上循环不管怎么算,都是注册失败
0040B47C |. E8 03ADFFFF CALL Flash2SC.00406184 ; 假码长度
0040B481 |. 83F8 2A CMP EAX,2A ; 和42比较,
0040B484 |. 0F85 BE010000 JNZ Flash2SC.0040B648 ; 如果不相等,注册失败
因此,我们断定,当注册码=24位时,没用。于是继续测试把假码就成 42 位的看看。
输入假码: 12345678909876543210ABCDEFGHIJKLMNOPQRSTUV (共42位)
当假码长度=42时,程序有效代码接着从下面开始:
0040B47C |. E8 03ADFFFF CALL Flash2SC.00406184 ; 假码长度
0040B481 |. 83F8 2A CMP EAX,2A ; 和42比较,
0040B484 |. 0F85 BE010000 JNZ Flash2SC.0040B648 ; 如果不相等,注册失败
0040B48A |. BE 457A4C00 MOV ESI,Flash2SC.004C7A45 ; 内置 (ASCII "1y1h+2a0n-0g8z*9a1n|"),记为 Str
0040B48F |. 8DBD 50FFFFFF LEA EDI,DWORD PTR SS:[EBP-B0]
0040B495 |. B9 05000000 MOV ECX,5
0040B49A |. F3:A5 REP MOVS DWORD PTR ES:[EDI],DWORD PTR DS>
0040B49C |. A4 MOVS BYTE PTR ES:[EDI],BYTE PTR DS:[ESI]
0040B49D |. 66:C745 EC 08>MOV WORD PTR SS:[EBP-14],8
0040B4A3 |. 8D45 0C LEA EAX,DWORD PTR SS:[EBP+C]
0040B4A6 |. E8 6977FFFF CALL Flash2SC.00402C14 ; 读取假码,记为 Sn
0040B4AB |. 50 PUSH EAX ; /Arg2
0040B4AC |. 8D95 68FFFFFF LEA EDX,DWORD PTR SS:[EBP-98] ; |
0040B4B2 |. 52 PUSH EDX ; |Arg1
0040B4B3 |. E8 F4CE0A00 CALL Flash2SC.004B83AC ; Flash2SC.004B83AC
0040B4B8 |. 83C4 08 ADD ESP,8
0040B4BB |. 0FBE4D 90 MOVSX ECX,BYTE PTR SS:[EBP-70]
0040B4BF |. 83F9 53 CMP ECX,53 ; 第41位必须是 S
0040B4C2 |. 0F85 80010000 JNZ Flash2SC.0040B648
0040B4C8 |. 0FBE45 91 MOVSX EAX,BYTE PTR SS:[EBP-6F]
0040B4CC |. 83F8 56 CMP EAX,56
0040B4CF |. 0F85 73010000 JNZ Flash2SC.0040B648 ; 第42位必须是 V
0040B4D5 |. 0FBE95 69FFFF>MOVSX EDX,BYTE PTR SS:[EBP-97]
0040B4DC |. 83FA 2A CMP EDX,2A ; 第2位必须是 *
0040B4DF |. 0F85 63010000 JNZ Flash2SC.0040B648
0040B4E5 |. C685 69FFFFFF>MOV BYTE PTR SS:[EBP-97],23 ; 把假码第2位变成#,此时的假码记为 Sn1
0040B4EC |. C645 DB 01 MOV BYTE PTR SS:[EBP-25],1 ; 标志位赋值=1(注册成功)
0040B4F0 |. C745 D0 02000>MOV DWORD PTR SS:[EBP-30],2 ; 初始化n=2
0040B4F7 |> 8B4D D0 /MOV ECX,DWORD PTR SS:[EBP-30] ; ECX = n
0040B4FA |. 0FBE840D 50FF>|MOVSX EAX,BYTE PTR SS:[EBP+ECX-B0] ; EAX = ord(Str[j]) (j初始化为3)
0040B502 |. 8B55 D0 |MOV EDX,DWORD PTR SS:[EBP-30] ; EDX = n
0040B505 |. 0FBE8C15 67FF>|MOVSX ECX,BYTE PTR SS:[EBP+EDX-99] ; ECX = ord(Sn1[n]);
0040B50D |. 03C1 |ADD EAX,ECX ; EAX + ECX
0040B50F |. 8B55 D0 |MOV EDX,DWORD PTR SS:[EBP-30] ; EDX = n
0040B512 |. 0FBE8C15 68FF>|MOVSX ECX,BYTE PTR SS:[EBP+EDX-98] ; ECX = ord(Sn1[n+1]);
0040B51A |. 33C1 |XOR EAX,ECX ; EAX = EAX xor ECX
0040B51C |. 8B55 D0 |MOV EDX,DWORD PTR SS:[EBP-30] ; EDX = n
0040B51F |. 0FBE8C15 50FF>|MOVSX ECX,BYTE PTR SS:[EBP+EDX-B0] ; EAX = ord(Str[j])
0040B527 |. 33C1 |XOR EAX,ECX ; EAX = EAX xor ECX
0040B529 |. 50 |PUSH EAX ; /Arg1
0040B52A |. E8 41010000 |CALL Flash2SC.0040B670 ; Flash2SC.0040B670
0040B52F |. 59 |POP ECX
0040B530 |. B9 1A000000 |MOV ECX,1A
0040B535 |. 99 |CDQ
0040B536 |. F7F9 |IDIV ECX
0040B538 |. 83C2 41 |ADD EDX,41 ; EDX = EAX mod $1A + $41
0040B53B |. 8B45 D0 |MOV EAX,DWORD PTR SS:[EBP-30]
0040B53E |. 0FBE8405 71FF>|MOVSX EAX,BYTE PTR SS:[EBP+EAX-8F] ; EAX指向假码第M位 (M从12开始到19)
0040B546 |. 3BD0 |CMP EDX,EAX ; EDX和EAX比较
0040B548 |. 74 06 |JE SHORT Flash2SC.0040B550 ; 如果不相等则注册失败
0040B54A |. C645 DB 00 |MOV BYTE PTR SS:[EBP-25],0 ; 标志位赋值=0(注册失败)
0040B54E |. EB 09 |JMP SHORT Flash2SC.0040B559
0040B550 |> FF45 D0 |INC DWORD PTR SS:[EBP-30]
0040B553 |. 837D D0 0A |CMP DWORD PTR SS:[EBP-30],0A
0040B557 |.^ 7C 9E JL SHORT Flash2SC.0040B4F7
0040B559 |> 807D DB 00 CMP BYTE PTR SS:[EBP-25],0 ; 通过上一个循环的验证了吗?
0040B55D |. 0F84 D5000000 JE Flash2SC.0040B638 ; 如果通过则继续
……以下暂时省略部分代码……
简述这个循环的过程,保证:
1、第41位是 S,第42位是 V,第2位是*
得出假码:1*345678909876543210ABCDEFGHIJKLMNOPQRSTSV
再临时把假码第二位就成#,即1#345678909876543210ABCDEFGHIJKLMNOPQRSTSV,记为 Sn1
然后通过一个循环验证Sn1第12-19位。具体步骤请看注释,不重复做解释了。(参见注册机源码)
我们可以通过把循环里面一句:
0040B548 74 06 JE SHORT Flash2SC.0040B550 ; 如果不相等则注册失败
改为
0040B548 EB 06 JMP SHORT Flash2SC.0040B550 ; 如果不相等则注册失败
然后看EAX和EDX的值,可以循环获得注册码的第12-19位为:IRNVLHHT
进一步把假码确认为:1*345678909IRNVLHHT0ABCDEFGHIJKLMNOPQRSTSV
下一个新断点在
0040B559 |> 807D DB 00 CMP BYTE PTR SS:[EBP-25],0 ; 通过上一个循环的验证了吗?
然后把其它断点全部去掉,然后输入上述假码,程序被断下,证明上面的验证都通过啦 ^_^
继续分析下面的代码:
0040B55D |. /0F84 D5000000 JE Flash2SC.0040B638 ; 如果通过则继续
0040B563 |. |C745 CC 18000>MOV DWORD PTR SS:[EBP-34],18 ; n = 24
0040B56A |. |66:C745 EC 08>MOV WORD PTR SS:[EBP-14],8
0040B570 |. |837D CC 28 CMP DWORD PTR SS:[EBP-34],28
0040B574 |. |7D 54 JGE SHORT Flash2SC.0040B5CA ; $18当然小于$28 -_-!! 不跳
0040B576 |> |8B55 CC /MOV EDX,DWORD PTR SS:[EBP-34] ; EDX = n
0040B579 |. |0FBE8415 51FF>|MOVSX EAX,BYTE PTR SS:[EBP+EDX-AF] ; EAX = ord(Sn1[j]) (j初始化为2)
0040B581 |. |B9 06000000 |MOV ECX,6
0040B586 |. |99 |CDQ
0040B587 |. |F7F9 |IDIV ECX
0040B589 |. |8BCA |MOV ECX,EDX ; ECX = EAX mod 6
0040B58B |. |8B45 CC |MOV EAX,DWORD PTR SS:[EBP-34] ; EAX = n
0040B58E |. |0FBE9405 52FF>|MOVSX EDX,BYTE PTR SS:[EBP+EAX-AE] ; EAX = ord(Sn1[j+1]) (j初始化为2)
0040B596 |. |D3E2 |SHL EDX,CL ; EDX = EDX shl CL
0040B598 |. |8B45 CC |MOV EAX,DWORD PTR SS:[EBP-34] ; EAX = n
0040B59B |. |0FBE8C05 53FF>|MOVSX ECX,BYTE PTR SS:[EBP+EAX-AD] ; ECX = ord(Sn[j+1])
0040B5A3 |. |0BD1 |OR EDX,ECX ; EDX = EDX or ECX
0040B5A5 |. |52 |PUSH EDX ; /Arg1
0040B5A6 |. |E8 C5000000 |CALL Flash2SC.0040B670 ; Flash2SC.0040B670
0040B5AB |. |59 |POP ECX
0040B5AC |. |B9 1A000000 |MOV ECX,1A
0040B5B1 |. |99 |CDQ
0040B5B2 |. |F7F9 |IDIV ECX
0040B5B4 |. |80C2 61 |ADD DL,61 ; DL = EAX mod $1A + $61
0040B5B7 |. |8B45 CC |MOV EAX,DWORD PTR SS:[EBP-34] ; EAX = n
0040B5BA |. |889405 24FFFF>|MOV BYTE PTR SS:[EBP+EAX-DC],DL ; 循环结果累加保存,记为 Tmp,(此处下断从内存可获得结果)
0040B5C1 |. |FF45 CC |INC DWORD PTR SS:[EBP-34] ; n = n + 1
0040B5C4 |. |837D CC 28 |CMP DWORD PTR SS:[EBP-34],28
0040B5C8 |.^|7C AC JL SHORT Flash2SC.0040B576 ; 小于40位时继续循环
0040B5CA |> |C685 4CFFFFFF>MOV BYTE PTR SS:[EBP-B4],5A ; Z
0040B5D1 |. |C685 4DFFFFFF>MOV BYTE PTR SS:[EBP-B3],59 ; 把Z,Y合并到 Tmp 的后面,(ovcplrkzreewqmcoZY),记为M
0040B5D8 |. |C745 C8 18000>MOV DWORD PTR SS:[EBP-38],18 ; n = 24
0040B5DF |. |66:C745 EC 08>MOV WORD PTR SS:[EBP-14],8
0040B5E5 |. |837D C8 28 CMP DWORD PTR SS:[EBP-38],28
0040B5E9 |. |7D 4D JGE SHORT Flash2SC.0040B638 ; 开始验证假码第25-40位了
0040B5EB |> |8B55 C8 /MOV EDX,DWORD PTR SS:[EBP-38] ; EDX = n
0040B5EE |. |0FBE8415 24FF>|MOVSX EAX,BYTE PTR SS:[EBP+EDX-DC] ; EAX = ord(M[j]) (j初始化为1)
0040B5F6 |. |C1E0 04 |SHL EAX,4 ; EAX = EAX shl 4
0040B5F9 |. |8B55 C8 |MOV EDX,DWORD PTR SS:[EBP-38] ; EDX = n
0040B5FC |. |0FBE8C15 25FF>|MOVSX ECX,BYTE PTR SS:[EBP+EDX-DB] ; ECX = ord(M[j+1])
0040B604 |. |D1F9 |SAR ECX,1 ; ECX = ECX sar 1
0040B606 |. |33C1 |XOR EAX,ECX ; EAX = EAX xor ECX
0040B608 |. |50 |PUSH EAX ; /Arg1
0040B609 |. |E8 62000000 |CALL Flash2SC.0040B670 ; Flash2SC.0040B670
0040B60E |. |59 |POP ECX
0040B60F |. |B9 1A000000 |MOV ECX,1A
0040B614 |. |99 |CDQ
0040B615 |. |F7F9 |IDIV ECX
0040B617 |. |83C2 41 |ADD EDX,41 ; EDX = EAX mod $1A + $41
0040B61A |. |8B45 C8 |MOV EAX,DWORD PTR SS:[EBP-38]
0040B61D |. |0FBE8405 68FF>|MOVSX EAX,BYTE PTR SS:[EBP+EAX-98] ; EAX逐位指向假码第25-40位
0040B625 |3BD0 |CMP EDX,EAX ; EAX和EDX比较,不相等则注册失败
0040B627 |74 06 JE SHORT Flash2SC.0040B62F 0040B629 |C645 DB 00 |MOV BYTE PTR SS:[EBP-25],0 ; 注册失败
0040B62D |. |EB 09 |JMP SHORT Flash2SC.0040B638
0040B62F |> |FF45 C8 |INC DWORD PTR SS:[EBP-38] ; inc (n)
0040B632 |. |837D C8 28 |CMP DWORD PTR SS:[EBP-38],28
0040B636 |.^|7C B3 JL SHORT Flash2SC.0040B5EB
0040B638 |> �FBE95 72FFFF>MOVSX EDX,BYTE PTR SS:[EBP-8E] ; EDX = 注册码第11位
这个过程有两个循环,第一个循环通过假码 Sn1 生成一个临时字符串:ovcplrkzreewqmco,记为Tmp
再合并Y,Z到后面,变成 ovcplrkzreewqmco,记为 M. 这个过程在注释里也非常明显地标明了,不再重复。
然后通过第二个循环通过M和Str的计算验证假码第25-40位是否正确,
尝试把
0040B627 /74 06 JE SHORT Flash2SC.0040B62F
改为
0040B627 /EB 06 JMP SHORT Flash2SC.0040B62F
便可以在
0040B625 3BD0 |CMP EDX,EAX ; EAX和EDX比较,不相等则注册失败
处下断看内存获得第25-40位真正注册码。
我已经记录下来,结果是:XBKARTNVQWFSKTJP,详细过程请看注册机源代码。
此时可以把假码进一步修正为:1*345678909IRNVLHHT0ABCDXBKARTNVQWFSKTJPSV
继续到最后一步验证了,
0040B638 |> �FBE95 72FFFF>MOVSX EDX,BYTE PTR SS:[EBP-8E] ; EDX = 注册码第11位
0040B63F |. 83FA 5A CMP EDX,5A ; EDX = 'Z'吗,不相等失败
0040B642 |. 74 04 JE SHORT Flash2SC.0040B648
0040B644 |. C645 DB 00 MOV BYTE PTR SS:[EBP-25],0 ; 注册失败
0040B648 |> 8A45 DB MOV AL,BYTE PTR SS:[EBP-25]
0040B64B |. 50 PUSH EAX
0040B64C |. FF4D F8 DEC DWORD PTR SS:[EBP-8]
0040B64F |. 8D45 0C LEA EAX,DWORD PTR SS:[EBP+C]
0040B652 |. BA 02000000 MOV EDX,2
0040B657 |. E8 44710B00 CALL Flash2SC.004C27A0
0040B65C |. 58 POP EAX
0040B65D |. 8B55 DC MOV EDX,DWORD PTR SS:[EBP-24]
0040B660 |. 64:8915 00000>MOV DWORD PTR FS:[0],EDX
0040B667 |. 5F POP EDI
0040B668 |. 5E POP ESI
0040B669 |. 8BE5 MOV ESP,EBP
0040B66B |. 5D POP EBP
0040B66C . C3 RETN
这一步非常简单,但却几乎让人崩溃 ~~~~~~~~~~~~~
因为它让我们前面的劳动白费,这一步到最后才验证注册码第11位必须是Z。
然而不能简单把假码第11位改成Z,
因为这一位之前已经参与到计算当中了,这一变动肯定会牵一发而动全身,得重新算一次这整个过程了。
因此,在逆向推算过程中,我们必须要有全局观念,把能预先能定下来的字字符先定,否则容易半途而废。
最后来一个总的算法逆向推算过程吧。
1、设有一假码42位。
2、保存第2位是*,第11位是Z,第41位是S,第42位是V
3、然后临时生成第1,第3-10位,第20-24位
4、通过循环计算得12-19位
5、通过循环计算得25-40位注册码
6、合并起来就是可用的注册码了。
不知道自己在讲什么,看Delphi源代码吧。function KeyGen:string;
var
Str:string;
n,j:integer;
n1,n2,n3:integer;
M,Tmp:string;
s1,s2:string;
Sn1, Sn3_10, Sn20_24:string;
Sn12_19, Sn25_40:string;
begin
Str:='1y1h+2a0n-0g8z*9a1n|'; //内置码;
Randomize;
//随机生成第3-10位
Sn3_10:=inttoHex(RandomRange($1000,$FFFF),4)+inttoHex(RandomRange($1000,$FFFF),4);
//准备生成注册码第12-19位
S1:='#'+Sn3_10+'Z'; //非常重要
Sn12_19:='';
for n:=1 to 8 do
begin
j:= n + 2; //从第3位开始取
n1:=(ord(Str[j]) + ord(S1[n])) xor ord(S1[n+1]) xor ord(Str[j]) ;
Sn12_19:= Sn12_19 + chr(n1 mod $1A + $41);
end;
//随机生成第20-24位
Sn20_24:= inttoHex(RandomRange($10000,$FFFFF),5);
S2:='#'+Sn3_10+'Z'+Sn12_19+Sn20_24;
//先生成临时串 Tmp (16位)
Tmp:='';
for n:=1 to 16 do
begin //取低位
n2:= (ord(S2[n+1]) shl (Lo(ord(S2[n]) mod 6))) or ord(S2[n+2]) ;
Tmp:=Tmp + chr((n2 mod $1A + $61));
end;
M:=Tmp + 'ZY';
//准备生成注册码第25-40位 (共16位)
Sn25_40:='';
for n:=1 to 16 do
begin
n3:= (ord(M[n]) shl 4) xor (ord(M[n+1]) div 2) ;
Sn25_40:=Sn25_40 + Chr((n3 mod $1A + $41));
end;
Sn1:=chr(RandomRange($41,$5A)); //随机生成第一位
Result:=Sn1+'*'+Sn3_10+'Z'+ Sn12_19+ Sn20_24+Sn25_40+'SV';
end;
最后给几组经上述代码计算出来的结果:
Q*429B75A7ZDQBBLUKM924FFMRVCMWBDEDXKQEORSV
H*D3BE20FBZHNDDLUACF8108APUCMNZISIQJFVXZSV
X*1F52486DZGBHZQEUK4B0CDMIJTTSAGUNSZGDMDSV
T*679FBB8EZFLIFCAWNAEC50APNEDJGECKSRWKEHSV
注册码保存在
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USERSoftwareXTZYFlash2SCR]
"NO"="M*1B01984AZGXOTUTSN7CE30WOVNBPDLBTAAKFXLSV"
软件破解只花半个小时,但写一篇完整的破文几乎搞了我一个下午,终于可以收工了。 ~~~
更多阅读
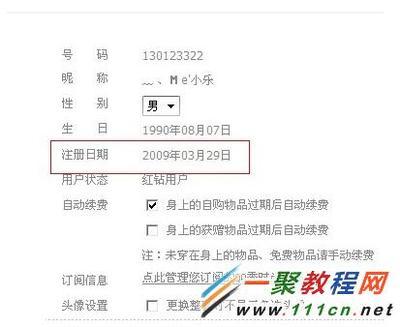
怎么查看QQ的注册时间?申请时间? 查看qq申请时间
怎么查看QQ的注册时间?申请时间?——简介查看QQ注册时间其实不难,但是也需要一些技巧,下面,我就来为你介绍几种方法:怎么查看QQ的注册时间?申请时间?——工具/原料QQ空间QQ秀WebQQ万年历终极办法怎么查看QQ的注册时间?申请时间?——方法/步骤怎

如何获得dota2的激活码? 如何获得百度云激活码
如何获得dota2的激活码?——简介dota 2已经登录国服,但是完美代理激活码一号难得,本文通过作者对相关信息整理,分享了几个获得方式 。如何获得dota2的激活码?——工具/原料dota2激活码获取方式有很多种,可以通过购买、也有少量免费激活码
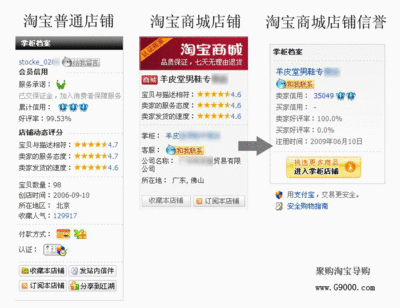
怎么看淘宝的注册日期? 淘宝注册日期怎么看
怎么看淘宝的注册日期?——简介淘宝网从成立至今,已走过十余年,而作为见证淘宝成长的广大用户来说,淘宝账号注册时间,则可看出我们什么时候就已成为马云背后的”女人“或”男人“,或许对于那些较真的用户来说,甚至想要具体到某一天,那究竟如
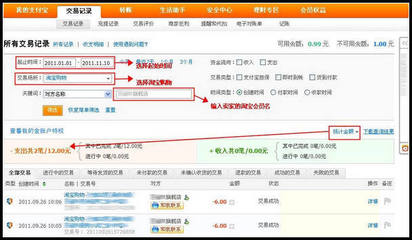
怎么查看淘宝的注册时间? 如何查看淘宝注册时间
怎么查看淘宝的注册时间?——简介怎么查看自己淘宝的注册时间?怎样查看淘宝的注册时间?怎么查看淘宝的注册时间?——工具/原料电脑怎么查看淘宝的注册时间?——方法/步骤怎么查看淘宝的注册时间? 1、登录淘宝账号怎么查看淘宝的注册时间
关于真实女友的去码补丁 使用 真实女友去码后图片
关于真实女友的去码补丁 使用——简介真实女友的补丁关于真实女友的去码补丁 使用——工具/原料去码补丁真实女友关于真实女友的去码补丁 使用——方法/步骤关于真实女友的去码补丁 使用 1、首先找到游戏目录下的 data 文件夹关
 爱华网
爱华网