| //DelphiSource unitUnit6; { C:ProgramFiles(x86)WEBZENMuGameGuardMuEng.ini [GAMEMON] GAME_NAME=MuEng UPDATE_SERVER=nprotect.muonline.webzen.net UPDATE_PATH=/GameGuard/MUGlobal/RealServer/ BACKUP_SERVER= BACKUP_PATH= OPTION_VALUE=0 SPEEDCHECK_INTERVAL=1000 GAMECRC=1 USE_GGSCAN=1 SENDERRLOG=3 LOG_SERVER=211.215.21.138 LIMIT_TYAVPDOWN=10 CHECK_GAMEBLOCK=1 USB_EJECT=1 C:ProgramFiles(x86)WEBZENMuMuEngTest.ini [GAMEMON] GAME_NAME=MuEngTest UPDATE_SERVER=nprotect.muonline.webzen.net UPDATE_PATH=/GameGuard/MUGlobal/TestServer/ BACKUP_SERVER= BACKUP_PATH= OPTION_VALUE=0 SPEEDCHECK_INTERVAL=1000 SENDERL=1 GAMECRC=1 USE_GGSCAN=1 SENDERRLOG=3 USE_PROXY=1 REVISION=47 LOG_SERVER=211.233.43.45 C:GamesMU1_08A+_FullMu.ini [GAMEMON] GAME_NAME=Mu UPDATE_SERVER=npro-mu.nefficient.co.kr UPDATE_PATH=/nProtect/GameGuard/MU/RealServer/ BACKUP_SERVER= BACKUP_PATH= OPTION_VALUE=0 SPEEDCHECK_INTERVAL=1000 SENDERL=1 GAMECRC=1 SENDERRLOG=1 USE_GGSCAN=1 REVISION=47 *) interface uses Winapi.Windows,Winapi.Messages,System.SysUtils,System.Variants,  System.Classes,Vcl.Graphics, Vcl.Controls,Vcl.Forms,Vcl.Dialogs,Vcl.StdCtrls,wcrypt2; type TForm6=class(TForm) Button1:TButton; Memo1:TMemo; procedureButton1Click(Sender:TObject); private {Privatedeclarations} public {Publicdeclarations} end; var Form6:TForm6; implementation {$R*.dfm} { Offset0123456789ABCDEF 000001904D752E696E69Mu.ini 000001A0006EA10959E65630CE02653C325E44FEnYęV0Īe<2^Dž 000001B02F67478CFAA8C8BC5F1D461DF4A55767/gGŒśØČ¼_FōWg 000001C0AC7ECB7B47D464F94D265BC0CD92D917¬~Ė{GŌdłM&[ĄĶ’Ł 000001D0AEE206149454690A9F9E30AFA2F4B3B2®ā”TiŸ˛0Æ¢ō³² 000001E068222681320700000040000000212681h"&2@!& 000001F0322 } procedureTForm6.Button1Click(Sender:TObject); type TGameGuard_Header=packedrecord FirstSignature:Cardinal; FileNameSize:Cardinal; SignatureSize:Cardinal; SecondSignature:Cardinal; end; PGameGuard_Header=^TGameGuard_Header; const FPUBKEY:array[0..83]ofByte=( $06,$02,$00,$00,$00,$24,$00,$00,$52,$53,$41,$31,$00,$02,$00, $00,$01,$00,$01,$00,$FB,$E3,$FC,$09,$AF,$AE,$65,$8C,$96,$4C, $C5,$37,$D2,$A4,$77,$E7,$4C,$41,$C2,$CF,$F2,$FE,$2D,$9C,$80, $94,$0C,$88,$6D,$B3,$84,$9F,$8C,$22,$A0,$C9,$CD,$C0,$AB,$30, $65,$82,$42,$3C,$EE,$3C,$A8,$B7,$11,$D6,$22,$FA,$FB,$23,$F7, $72,$CD,$E7,$D0,$6F,$6A,$8E,$96,$E3); KEY:array[0..9]ofByte=($65,$63,$74,$47,$61,$6D,$65,$4D,$6F,$6E); (* DataHdr:array[0..89]ofbyte=( $4D,$75,$45,$6E,$67,$2E,$69,$6E,$69,$00,//name $35,$3C,$05,$11,$01,$07,$24,$B5,$6A,$19,$B2,$A8,$38,$F6,$BD,$E3,//sig $21,$7A,$03,$20,$5B,$97,$72,$71,$1F,$36,$48,$B5,$E1,$CB,$9C,$01,//na $AA,$21,$DE,$CA,$B4,$6E,$D0,$DD,$53,$0B,$11,$A8,$67,$EC,$CD,$E4,//tu $8D,$BA,$E2,$23,$9C,$74,$E7,$33,$BF,$F6,$9D,$3A,$66,$BC,$1B,$D6,//re $22,$26,$81,$32,//keyF $0A,$00,$00,$00,//FileName-10 $40,$00,$00,$00,//Signatureslen-64 $21,$26,$81,$32//KeyS ); *) SIGNATURE1=$32812622; SIGNATURE2=$32812621; var Fs:TStream; Buffer:TBytes; Header:TGameGuard_Header; Len:DWORD; Signature:TBytes; i:Integer; Result:string; hProv:HCRYPTPROV; hHash:HCRYPTHASH; hKey:HCRYPTKEY; begin try Fs:=TFileStream.Create('C:UsersRonaldoDownloadsupdate(1).cfg',fmOpenRead); try SetLength(Buffer,Fs.Size); Fs.ReadBuffer(Buffer[0],Length(Buffer)); finally Fs.Free; end; except end; Len:=Length(Buffer); Len:=Len-SizeOf(TGameGuard_Header); Header:=PGameGuard_Header(@Buffer[Len])^; Len:=Len-(Header.FileNameSize+Header.SignatureSize); ifnot(SIGNATURE1=Header.FirstSignature)ornot(SIGNATURE2=Header.SecondSignature)then MessageDlg('0',mtWarning,[mbOK],0); SetLength(Signature,Header.SignatureSize); Move(Buffer[Len+Header.FileNameSize],Signature[0],Length(Signature)); ifnotCryptAcquireContext(@hProv,nil,MS_DEF_PROV,PROV_RSA_FULL,CRYPT_VERIFYCONTEXT)then MessageDlg('1',mtWarning,[mbOK],0); ifnotCryptCreateHash(hProv,CALG_MD5,0,0,@hHash)then MessageDlg('2',mtWarning,[mbOK],0); ifnotCryptImportKey(hProv,@FPUBKEY[0],SizeOf(FPUBKEY),0,0,@hKey)then MessageDlg('3',mtWarning,[mbOK],0); ifnotCryptHashData(hHash,@Buffer[0],len+Header.FileNameSize,0)then MessageDlg('4',mtWarning,[mbOK],0); ifnotCryptVerifySignature(hHash,@Signature[0],Header.SignatureSize,hKey,nil,0)then MessageDlg('5',mtWarning,[mbOK],0); CryptDestroyKey(hKey); CryptDestroyHash(hHash); ifnotCryptCreateHash(hProv,CALG_MD5,0,0,@hHash)then MessageDlg('6',mtWarning,[mbOK],0); ifnotCryptHashData(hHash,@KEY[0],SizeOf(KEY),0)then MessageDlg('7',mtWarning,[mbOK],0); ifnotCryptDeriveKey(hProv,CALG_RC4,hHash,0,@hKey)then MessageDlg('8',mtWarning,[mbOK],0); ifnotCryptDecrypt(hKey,0,True,0,@Buffer[0],@Len)then MessageDlg('9',mtWarning,[mbOK],0); CryptDestroyKey(hKey); CryptDestroyHash(hHash); CryptReleaseContext(hProv,0); fori:=0toLen-1do Result:=Result+Chr(Buffer[i]); Memo1.Clear; Memo1.Lines.Add(Result) end; end.
|
解密gameguard*.ini,*.cfg文件源码 ctce8.cfg 解密
更多阅读

股票公式全解析:16 股票软件源码引入
股票公式全解析:[16]股票软件源码引入——简介我们上一篇文章主要说明了大智慧的源码引入的基本方法,大家在使用这个源码的时候一定要注意具体的设置,按照我的要求一步一步实现,源码的编写我会专门有一个介绍,现在我继续说明其他股票软件
易语言进度条源码 精易论坛
易语言进度条源码——简介今天,我给大家带来如何弄进度条!易语言进度条源码——工具/原料电脑易语言易语言进度条源码——方法/步骤易语言进度条源码 1、打开易语言!拉
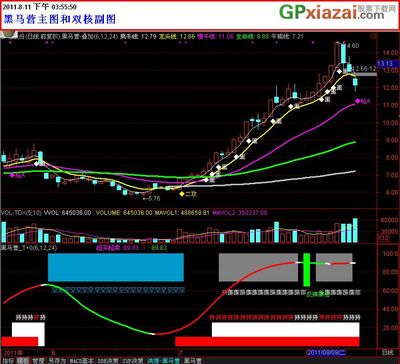
绝对比美黑马赢家的黑马营通达信主图、双核及系列选股公式源码 宜兴环保黑马营
1、回马枪B公式源码:当日成本:=IF(C>REF(C,1),(3*H+4*C+3*OPEN+2*L)/12,(2*H+4*C+3*OPEN+3*L)/12);疯牛线:=EXPMEMA(当日成本,3);龙头线:=EXPMEMA(当日成本,8);慢牛线:=EXPMEMA(当日成本,25);生命线:=EXPMEMA(当日成本,79);牛熊线:=

windows中下载android源码 android系统源码下载
由于ubuntu出现问题了,repogit下载android总是出现问题,因此寻求在windows下下砸android的源码1. 进入http://code.google.com/p/msysgit/下载最新的Git-1.7.0.2-pr
动态百分比公式源码! 百分比计算公式
动态百分比公式源码!a1:=hhv(h,256);a2:=llv(l,256);m1:ma(c,64);m2:ma(c,256);k1:(0.618*a1+0.382*a2);k2:(0.5*a1+0.5*a2);k3:(0.382*a1+0.618*a2);说明:一 代码说明
 爱华网
爱华网